A new Node.js based remote access trojan and password-stealing malware is being distributed through malicious emails pretending to be from the U.S. Department of the Treasury.
This new spam campaign was discovered by Abuse.ch that says payment for a government contract was not paid due to incorrect banking information.
The email then prompts the user to examine the document for any mistakes, as if they do not hear back, the money will be used of the government's Coronavirus disaster relief.
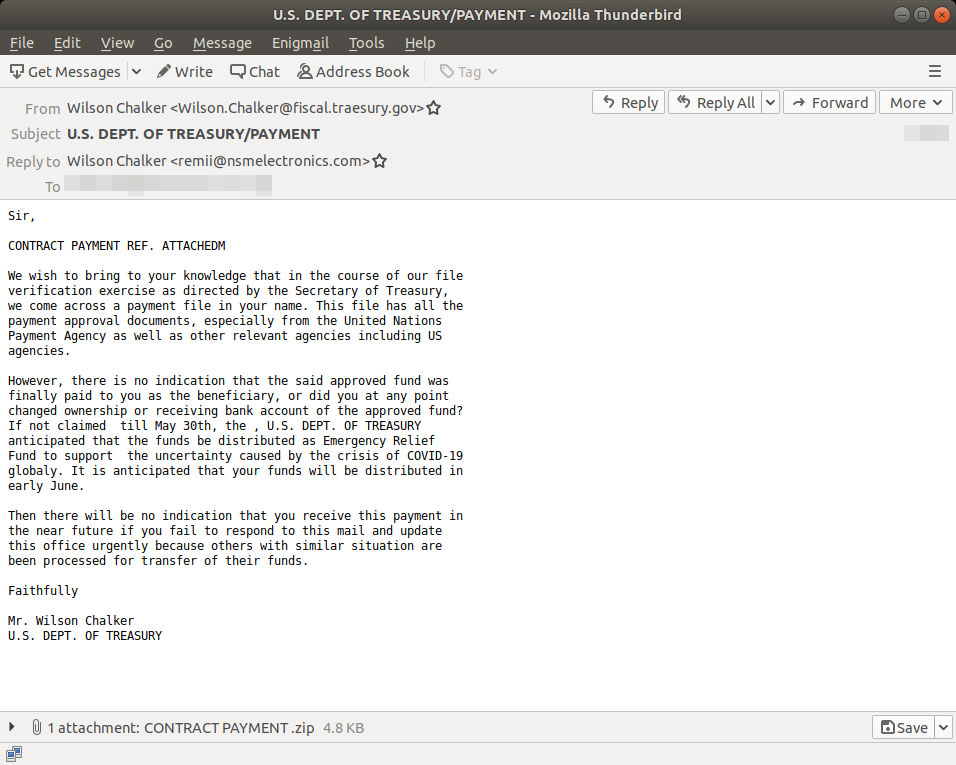
"However, there is no indication that the said approved fund was finally paid to you as the beneficiary, or did you at any point changed ownership or receiving bank account of the approved fund? If not claimed till May 30th, the , U.S. DEPT. OF TREASURY anticipated that the funds be distributed as Emergency Relief Fund to support the uncertainty caused by the crisis of COVID-19 globaly. It is anticipated that your funds will be distributed in early June," the phishing email states.
Attached to this email is an archive named 'CONTRACT PAYMENT.zip' containing a file named 'CONTRACT PAYMENT.jar'.
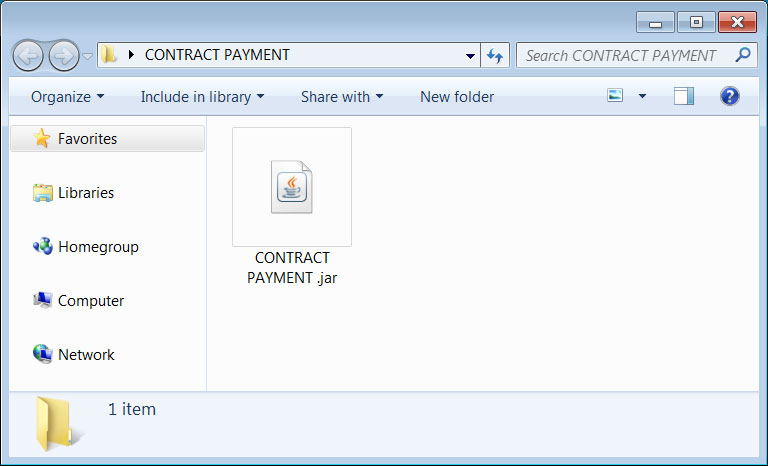
This malware is a new Node.js malware called QNodeService that was discovered by MalwareHunterTeam and later analyzed by TrendMicro.
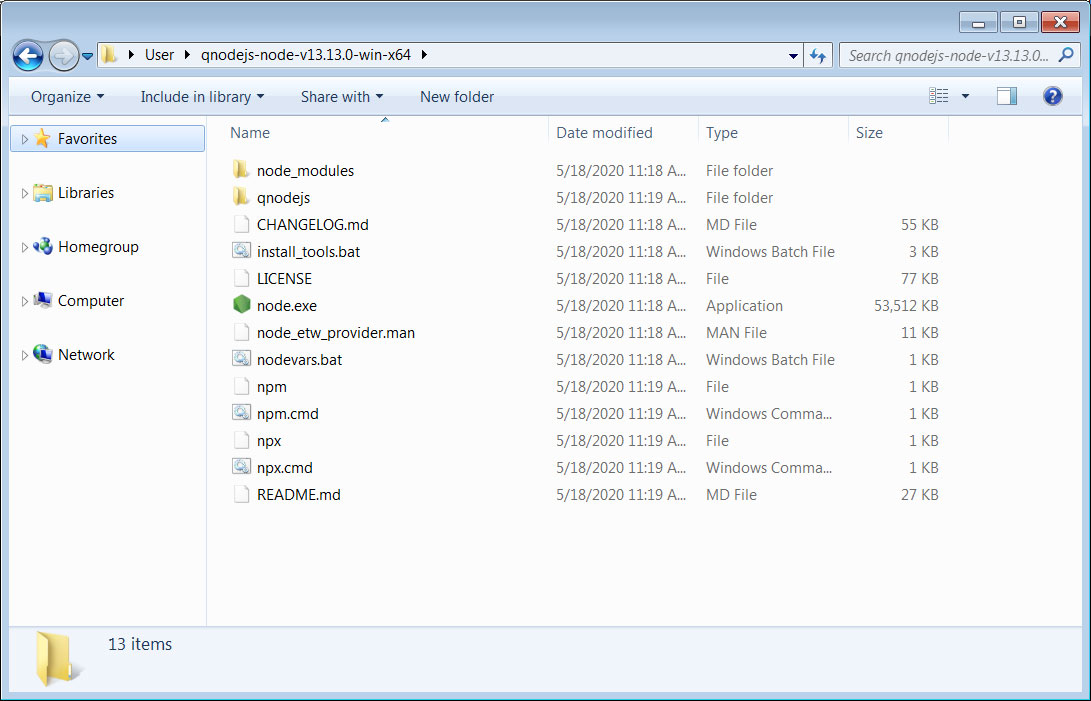
When executed, this JAR file will download Node.js and a script called wizard.js and stored the packages in a folder named %UserProfile\qnodejs-node-v13.13.0-win-x64, as seen below.
So that the malware is run every time the victim logs into Windows, a Windows Registry Run value will be created.
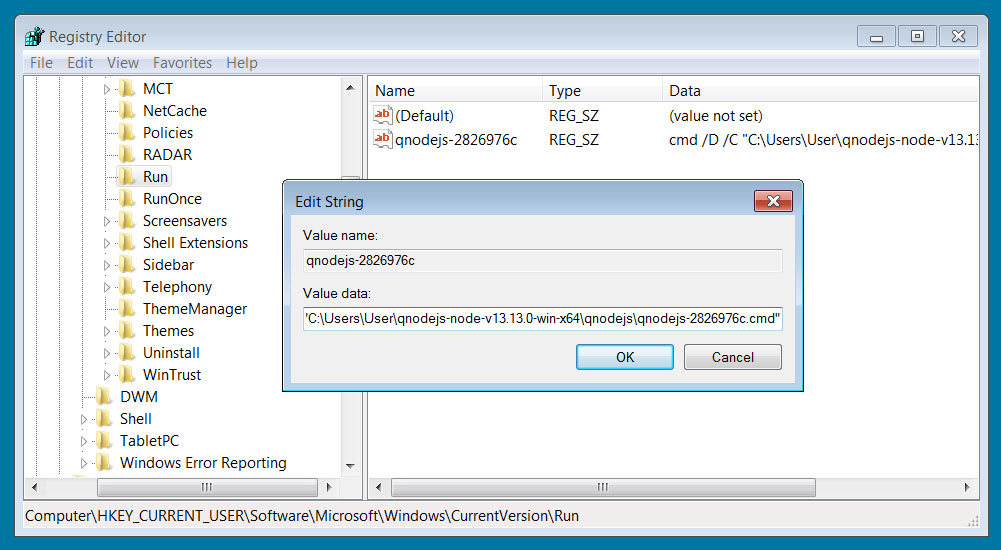
According to TrendMicro's report, once the QNodeService is installed, it will have full control over the computer and further compromise it to steal data.
This further compromise is made through the following features built into the QNodeService malware:
- Update itself
- Get machine information such as IP address, machine name, location, user name, and OS version.
- Execute commands, including the download of further payloads.
- Delete and write files
- Steal passwords from various applications such as Chrome and Firefox.
If you have fallen victim to this malware, you should immediately assume that your data and passwords have been compromised.
It is also possible that the malware was used to gain access to other devices on your network.
Due to this, you should immediately change any passwords that you have saved in your browser's or other applications.
Network, system, and security administrators should then perform an audit of the rest of the network to confirm that no other devices were compromised.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now